AWS EKS Cluster Creation - Complete Guide to Kubernetes Cluster Setup
IAM user needs following permissions: EKS, IAM, CloudFormation, VPC.
This document prescribes how to create an AWS EKS Cluster using the AWS console, and AWS cli too.
An EKS cluster is basically setup in TWO parts: the Cluster part (IAM and create control plane), the managed Node part (IAM and create managed nodes).
AWS Console
Reference: EKS User Guide: Create Cluster
Pre-requisites
- VPC
aws clikubectli.e.curl -O https://s3.us-west-2.amazonaws.com/amazon-eks/1.27.1/2023-04-19/bin/linux/amd64/kubectlfor Linux
(optional) install eksctl
For Linux users (obvs):
# for ARM systems, set ARCH to: `arm64`, `armv6` or `armv7`
ARCH=amd64
PLATFORM=$(uname -s)_$ARCH
curl -sLO "https://github.com/eksctl-io/eksctl/releases/latest/download/eksctl_$PLATFORM.tar.gz"
# (Optional) Verify checksum
curl -sL "https://github.com/eksctl-io/eksctl/releases/latest/download/eksctl_checksums.txt" | grep $PLATFORM | sha256sum --check
tar -xzf eksctl_$PLATFORM.tar.gz -C /tmp && rm eksctl_$PLATFORM.tar.gz
sudo mv /tmp/eksctl /usr/local/bin
You need to set a few things up first before you create your EKS Cluster, and Node Groups.
First, you need a EKS compatible VPC via CloudFormation.
- Go to https://console.aws.amazon.com/cloudformation/.
- Create stack:
- Template is ready
- Amazon S3 URL =
https://s3.us-west-2.amazonaws.com/amazon-eks/cloudformation/2020-10-29/amazon-eks-vpc-private-subnets.yaml(creates public & private subnet VPC)
- Click through until
Submit
You have a VPC - private subs for Nodes, public subs for LBs to Nodes.
Now you need to create TWO IAM Roles.
IAM Role - Cluster
This is the IAM Role for EKS to use to work with the cluster.
- Go to https://us-east-1.console.aws.amazon.com/iamv2/home
- Create Role,
- Trusted entity type:
AWS Service - Use case: EKS, EKS - Cluster
- Add Permissions:
AmazonEKSClusterPolicy - Role name:
AmazonEKSClusterRole - Check Select trusted entities looks like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": [
"eks.amazonaws.com"
]
},
"Action": "sts:AssumeRole"
}
]
}
Done.
IAM Role - Node Group
Reference: EKS User Guide: Create Node Role
- Go to https://us-east-1.console.aws.amazon.com/iamv2/home
- Create a new role name
AmazonEKSNodeGroupRole. - Find & Attach the following policies:
AmazonEKSWorkerNodePolicyAmazonEC2ContainerRegistryReadOnlyAmazonEKS_CNI_Policy
Create EKS Cluster
- go to https://ap-southeast-2.console.aws.amazon.com/eks/home?region=ap-southeast-2#/cluster-create
- create a cluster
- add Name, Kubernetes version, select cluster role
AmazonEKSClusterRole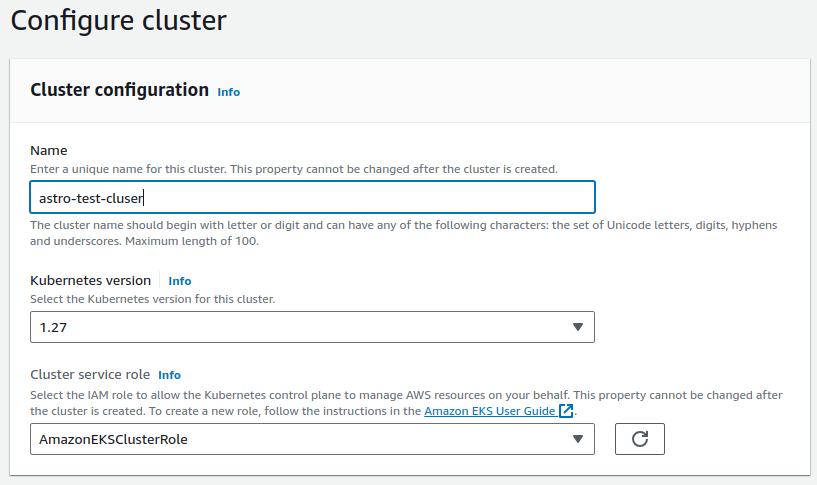
- Next, select the VPC from the pre-reqs, created by cloudformation
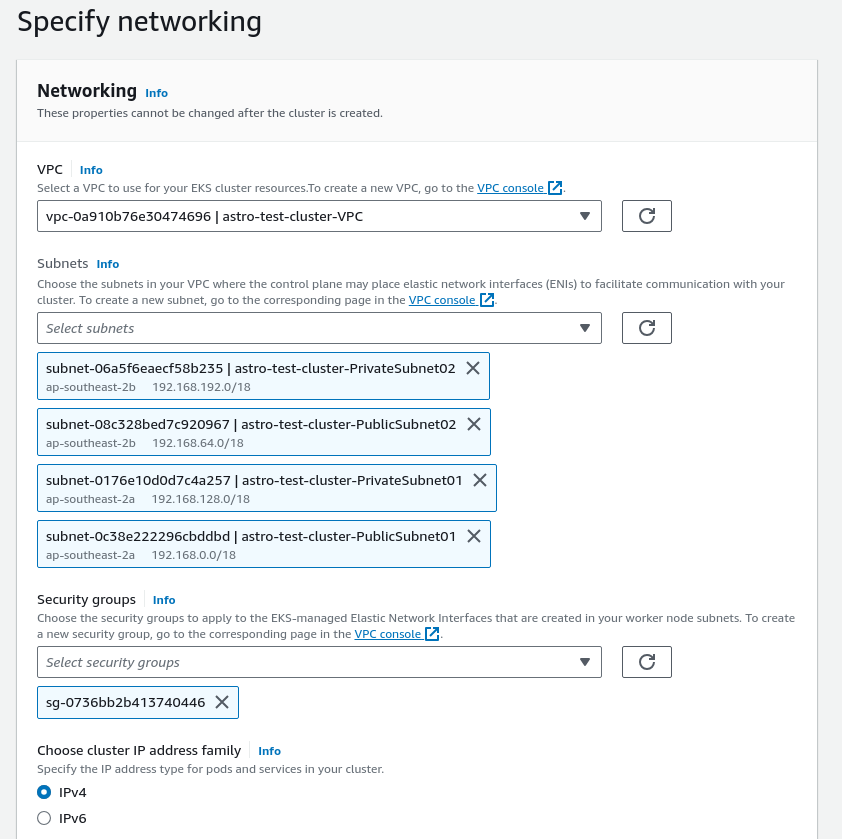
- select ALL subnets.
- select Security Group from the VPC created by cloudformation.
- cluster endpoint access = "Public and private"
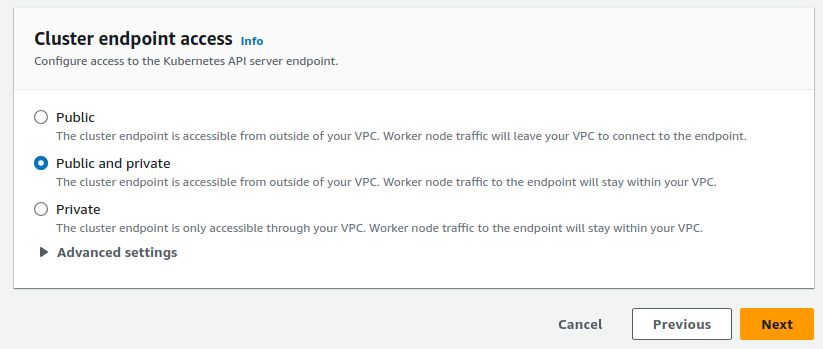
- Next, Add-ons you should see
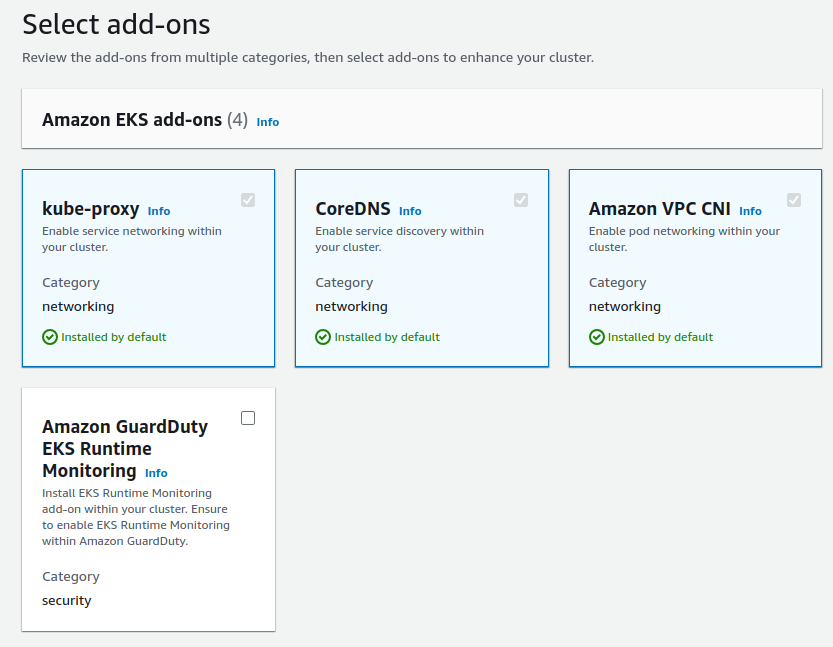
- kube-proxy
- CoreDNS
- Amazon VPC CNI
- Next, Next, Create.
Wait for your cluster to become active, then onto creating the node groups (data plane).
Create Node Groups
- go to your cluster
- go to
Compute - go down to
Node groupsand clickAdd node group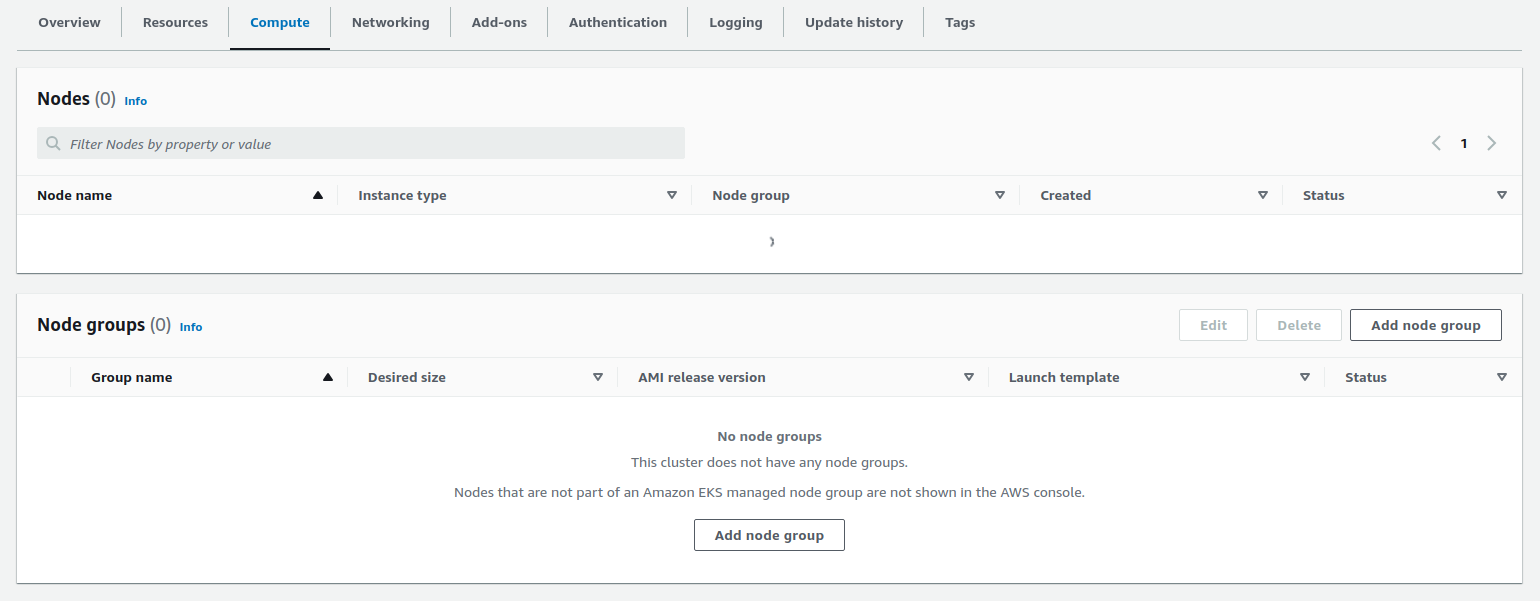
- create a name, and select the
AmazonEKSNodeGroupRolefor Node IAM role.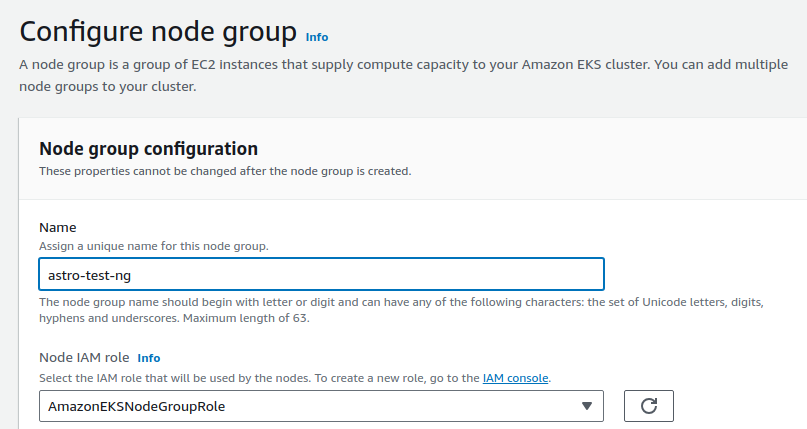
- Next, choose your AMI and instance settings.
- Next, because we have both public & private subnets, de-select public subnets we are deploying Nodes to private subnets only.
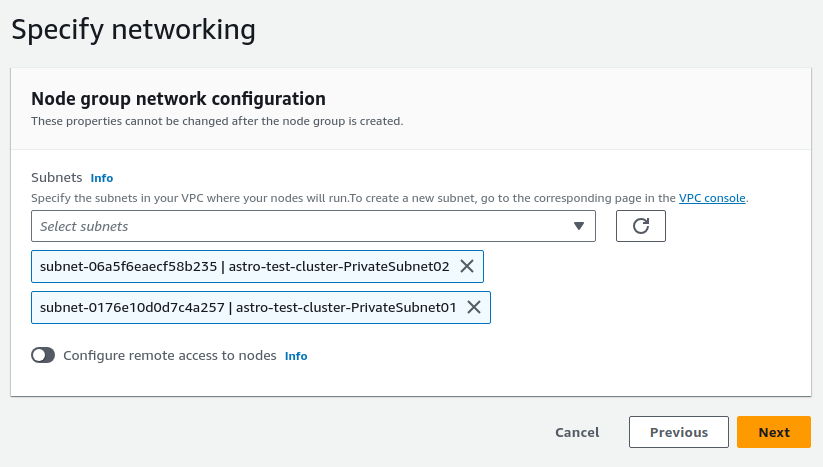
- Next, Create.
When your nodes are ready in EC2, you'll see them and the Node group ready here: 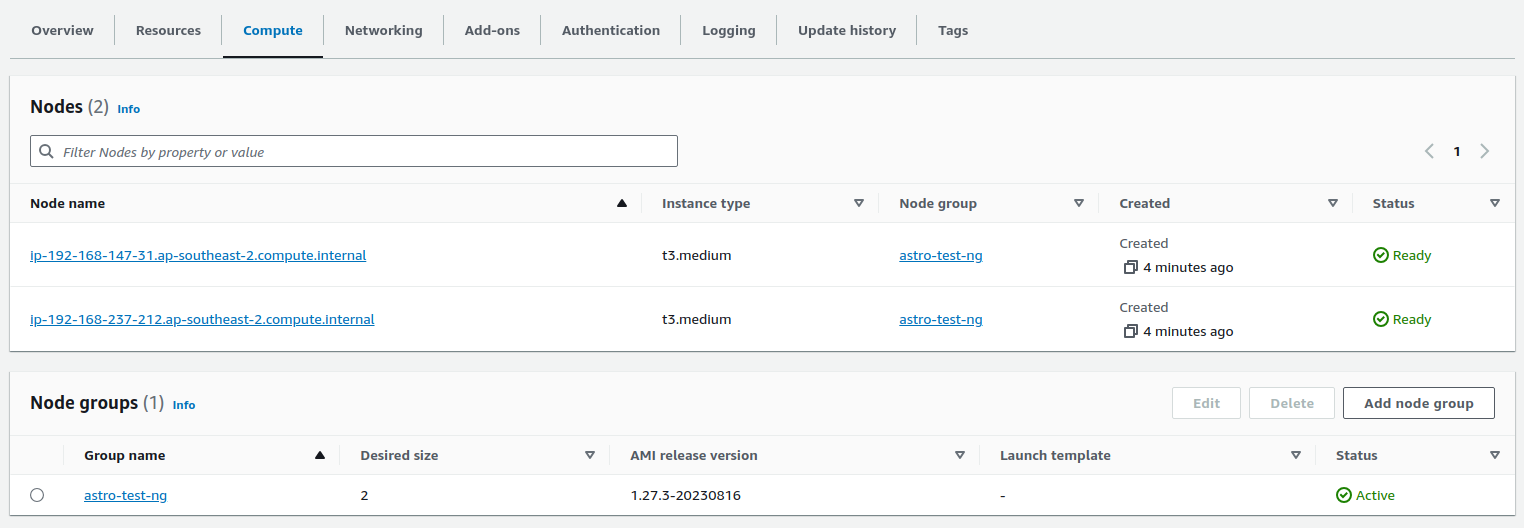
Setup kubeconfig
- configure your
aws cliwith access key, secret for your user. - run
aws eks update-kubeconfig --region region-code --name my-clusteri.e.aws eks update-kubeconfig --region ap-southeast-2 --name astro-test-cluster
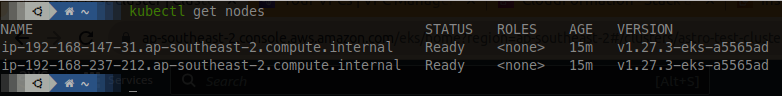
and voila, you have a running and cli-accessible EKS cluster:
AWS CLI
The quick version of running everything from the aws cli, you can choose to install via eksctl that's another option.
I assume you have the prerequisites installed, so we'll just run over the commands for each section covered in the console version.
VPC from cloudformation
aws cloudformation create-stack \
--region region-code \
--stack-name my-eks-vpc-stack \
--template-url https://s3.us-west-2.amazonaws.com/amazon-eks/cloudformation/2020-10-29/amazon-eks-vpc-private-subnets.yaml
IAM Roles & Cluster
Create JSON with the EKS trust policy:
cat >eks-cluster-role-trust-policy.json <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "eks.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
EOF
- create
AmazonEKSClusterRoleby running command:aws iam create-role --role-name AmazonEKSClusterRole --assume-role-policy-document file://"eks-cluster-role-trust-policy.json" - attach policy :
aws iam attach-role-policy --policy-arn arn:aws:iam::aws:policy/AmazonEKSClusterPolicy --role-name AmazonEKSClusterRole
IAM Roles & Nodes
This is the node role trust policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
- create
AmazonEKSNodeGroupRolesby running command:aws iam create-role --role-name AmazonEKSNodeGroupRole --assume-role-policy-document file://"node-role-trust-policy.json" - attach the 3 x policies:
aws iam attach-role-policy \
--policy-arn arn:aws:iam::aws:policy/AmazonEKSWorkerNodePolicy \
--role-name AmazonEKSNodeGroupRole
aws iam attach-role-policy \
--policy-arn arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly \
--role-name AmazonEKSNodeGroupRole
aws iam attach-role-policy \
--policy-arn arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy \
--role-name AmazonEKSNodeGroupRole
Create cluster using CLI
aws eks create-cluster --region region-code --name demo-cluster --kubernetes-version 1.27 \
--role-arn arn:aws:iam::111122223333:role/AmazonEKSClusterRole \
--resources-vpc-config subnetIds=subnet-ExampleID1,subnet-ExampleID2,securityGroupIds=sg-ExampleID1
some aws cli commands to grab these details:
# IAM Role ARN
aws iam get-role --role-name AmazonEKSClusterRole --query 'Role.Arn'
# VPC Subnets
aws ec2 describe-subnets --filters "Name=vpc-id,Values=vpc-068959db5aa05a1bb" --query 'Subnets[*].SubnetId'
# Security Group based VPC id
aws ec2 describe-security-groups --filters "Name=vpc-id,Values=<VPC-ID />"
Create Node Group using CLI
aws eks create-nodegroup \
--cluster-name <CLUSTER-NAME /> \
--nodegroup-name <NODEGROUP-NAME /> \
--subnets <SUBNET-ID1 /> <SUBNET-ID2 /> \
--node-role <NODE-ROLE-ARN /> \
--ami-type <AMI-TYPE /> \
--scaling-config minSize=<MIN-SIZE />,maxSize=<MAX-SIZE />,desiredSize=<DESIRED-SIZE />
e.g.
aws eks create-nodegroup \
--cluster-name demo-cluster \
--nodegroup-name demo-ng \
--subnets subnet-080e38b1842fc3c2d subnet-0cc6119f1dd9f1657 \
--node-role arn:aws:iam::1111111111111:role/AmazonEKSNodeGroupRole \
--ami-type AL2_x86_64 \
--scaling-config minSize=2,maxSize=2,desiredSize=2
use some commands from above to grab some details
# EKS optimised AMI id's
aws ssm get-parameter --name /aws/service/eks/optimized-ami/1.27/amazon-linux-2/recommended/image_id --region ap-southeast-2 --query "Parameter.Value" --output text
Get your kubeconfig setup:
`aws eks update-kubeconfig --region region-code --name my-cluster` i.e. `aws eks update-kubeconfig --region ap-southeast-2 --name demo-cluster`
Demo Application
Deploy the AWS Retail Store App.
Credits
- big s/o to Kavitha Suresh Kumar video for a great video that quickly cuts through the process.
- AWS Documentation as noted above.